Scenario
In this Sherlock activity, players will examine artefacts and logs from a Domain Controller, as well as endpoint artefacts from where Kerberoast attack activity originated. We will explore what to look for to properly identify Kerberoasting attack activity and how to avoid false positives given the complexity of Active Directory.
Questions
Questions
- Analyzing Domain Controller Security Logs, can you confirm the date & time when the kerberoasting activity occurred?
- What is the Service Name that was targeted?
- It is really important to identify the Workstation from which this activity occurred. What is the IP Address of the workstation?
- Now that we have identified the workstation, a triage including PowerShell logs and Prefetch files are provided to you for some deeper insights so we can understand how this activity occurred on the endpoint. What is the name of the file used to Enumerate Active directory objects and possibly find Kerberoastable accounts in the network?
- When was this script executed?
- What is the full path of the tool used to perform the actual kerberoasting attack?
- When was the tool executed to dump credentials?
Analysis
C:.
└───Triage
├───Domain Controller
│ SECURITY-DC.evtx
│
└───Workstation
│ Powershell-Operational.evtx
│
└───2024-05-21T033012_triage_asset
└───C
└───Windows
└───prefetch
ACE2016-KB5002138-FULLFILE-X6-F6B4ABCD.pf
APPLICATIONFRAMEHOST.EXE-8CE9A1EE.pf
AUDIODG.EXE-AB22E9A6.pf
BACKGROUNDTASKHOST.EXE-F8B2DD01.pf
CMD.EXE-0BD30981.pf
<SNIP>
WMIADAP.EXE-BB21CD77.pf
WMIPRVSE.EXE-E8B8DD29.pf
WUAUCLT.EXE-5D573F0E.pf
WWAHOST.EXE-2CFA09D4.pfThe Sherlock provides use with a few Windows artifacts from a Domain Controller and a Workstation. I start of by processing the .evtx files with EvtxCmd and the Prefetch files with PECmd
PECmd.exe -d .\Triage\Workstation\2024-05-21T033012_triage_asset\C\Windows\prefetch\ --csv . --csvf prefetch.workstation
EvtxECmd.exe -f .\Triage\Workstation\Powershell-Operational.evtx --csv . --csvf PS-Operational.workstation
EvtxECmd.exe -f '.\Triage\Domain Controller\SECURITY-DC.evtx' --csv . --csvf security.dcKerberoasting
Kerberoasting by HackTricks
Kerberoasting focuses on the acquisition of TGS tickets, specifically those related to services operating under user accounts in Active Directory (AD), excluding computer accounts. The encryption of these tickets utilizes keys that originate from user passwords, allowing for the possibility of offline credential cracking. The use of a user account as a service is indicated by a non-empty “ServicePrincipalName” property. Kerberoasting tools typically request
**RC4 encryption**when performing the attack and initiating TGS-REQ requests. This is because RC4 is weaker and easier to crack offline using tools such as Hashcat than other encryption algorithms such as AES-128 and AES-256. https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/kerberoast
Detecting Kerberoasting
Detecting Kerberoasting by MITRE
Monitor for anomalous Kerberos activity, such as enabling Audit Kerberos Service Ticket Operations to log Kerberos TGS service ticket requests. Particularly investigate irregular patterns of activity (ex: accounts making numerous requests, Event ID 4769, within a small time frame, especially if they also request RC4 encryption [Type 0x17]). https://attack.mitre.org/techniques/T1558/003/
Now based of this information I filter the Security Eventlog of the Domain Controller using the following filter.
Contains([Payload Data4], 'RC4-HMAC') And [Event Id] In (4768, 4769)This tells use that the attacker performed the Kerberoasting at 2024-05-21 03:18:09 against the service FORELA.LOCAL\MSSQLService from with a source IP of 172.17.79.129.
Workstation Artifacts
Prefetch Files
Now armed with the knowledge of when and where it is time to dig deeper into the client activity around the time the Kerberoasting took place. A good place to start is the Prefetch timeline generated by Eric Zimmermans PECmd tool.
IsSameDay([Run Time], #2024-05-21#)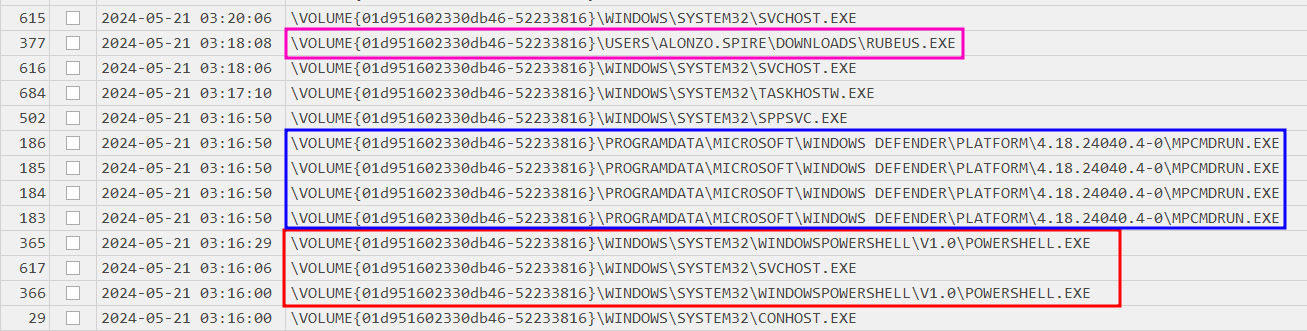
Closing in on the time of the Kerberoasting shows some potentially interesting events.
- (red) while Powershell in and of itself is not a definitive indicator of malicious activity since we know something happened those processes might be related
- (blue) some WindowsDefender activity
- (pink) most certainly malicious activity → Rubeus is a well known tool perform a multitude of attacker techniques related to Active Directory.
So we know that the attacker used C:\USERS\ALONZO.SPIRE\DOWNLOADS\RUBEUS.EXE at 2024-05-21 03:18:08 to perform the Kerberoasting but not how they enumerated the AD.
Powershell Operational EVTX
The malicious activity is visible on first glance when looking at the Powershell-Operational eventlog. Since thankfully ScriptBlockLogging was enabled on the workstation the executed script was captured in its entirety .
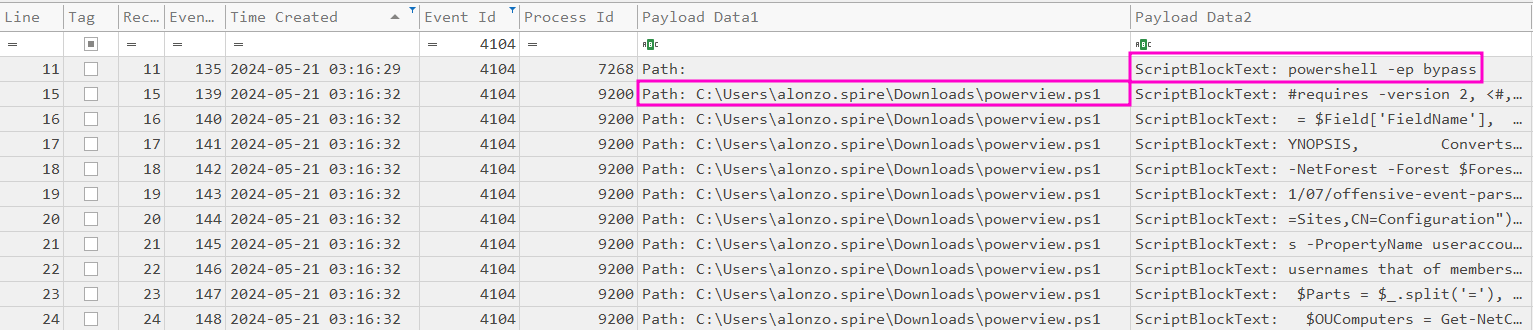
So we now known the attacker started a new Powershell process with powershell -ep bypass at 2024-05-21 03:16:29 to set the ExecutionPolicy to allow his script to run. And than ran the PowerView script C:\Users\alonzo.spire\Downloads\powerview.ps1 at 2024-05-21 03:16:32
Answers
Answers
- Analyzing Domain Controller Security Logs, can you confirm the date & time when the kerberoasting activity occurred?
2024-05-21 03:18:09→ DC security.evtx
- What is the Service Name that was targeted?
MSSQLService→ DC security.evtx
- It is really important to identify the Workstation from which this activity occurred. What is the IP Address of the workstation?
172.17.79.129→ DC security.evtx
- Now that we have identified the workstation, a triage including PowerShell logs and Prefetch files are provided to you for some deeper insights so we can understand how this activity occurred on the endpoint. What is the name of the file used to Enumerate Active directory objects and possibly find Kerberoastable accounts in the network?
powerview.ps1→ workstation PS-operational
- When was this script executed?
2024-05-21 03:16:32→ workstation PS-operational
- What is the full path of the tool used to perform the actual kerberoasting attack?
C:\Users\Alonzo.spire\Downloads\Rubeus.exe→ prefetch
- When was the tool executed to dump credentials?
2024-05-21 03:18:08→ prefetch